A risk assessment without structure? Much too risky.
1. You have no common, systematic model to start from.
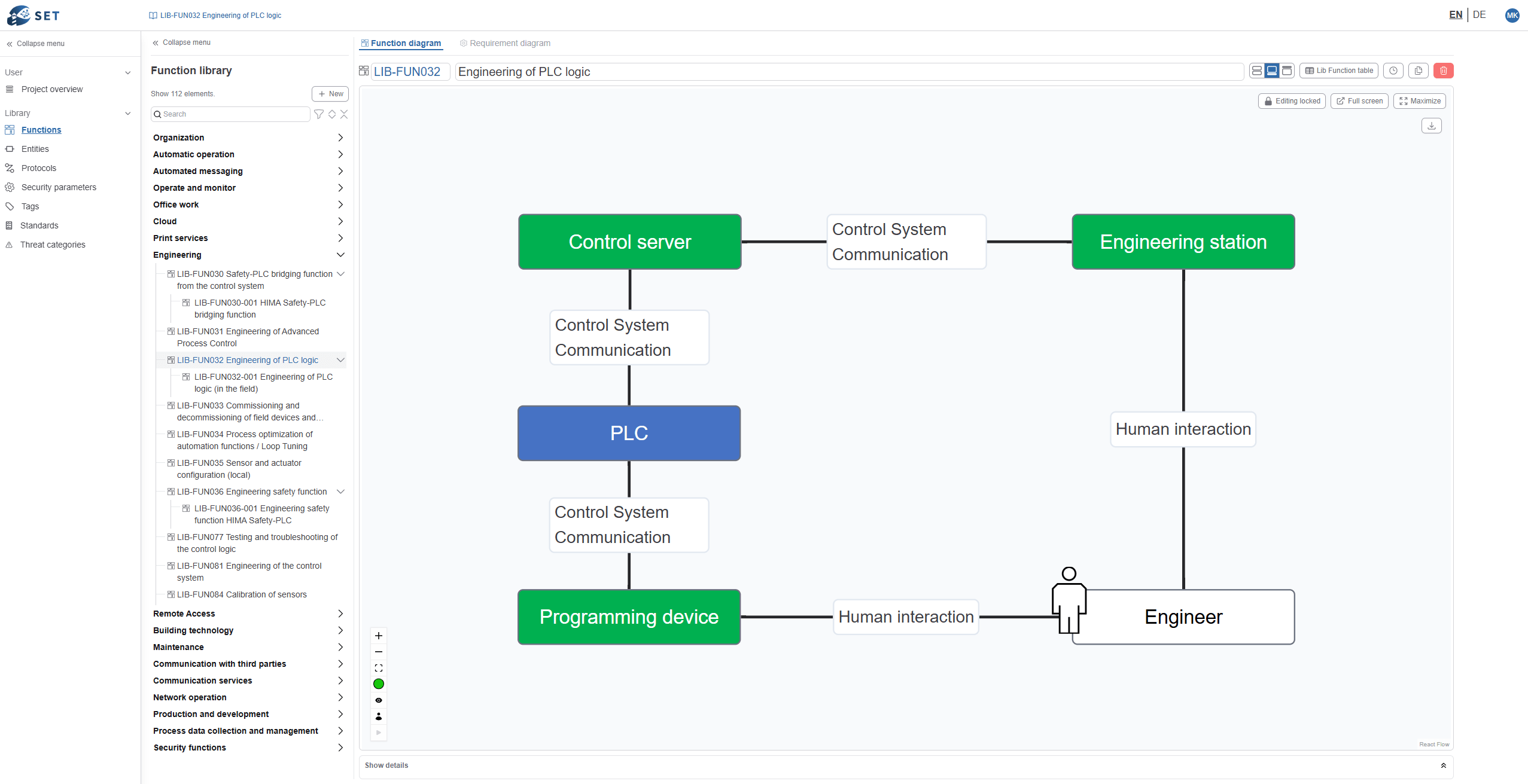
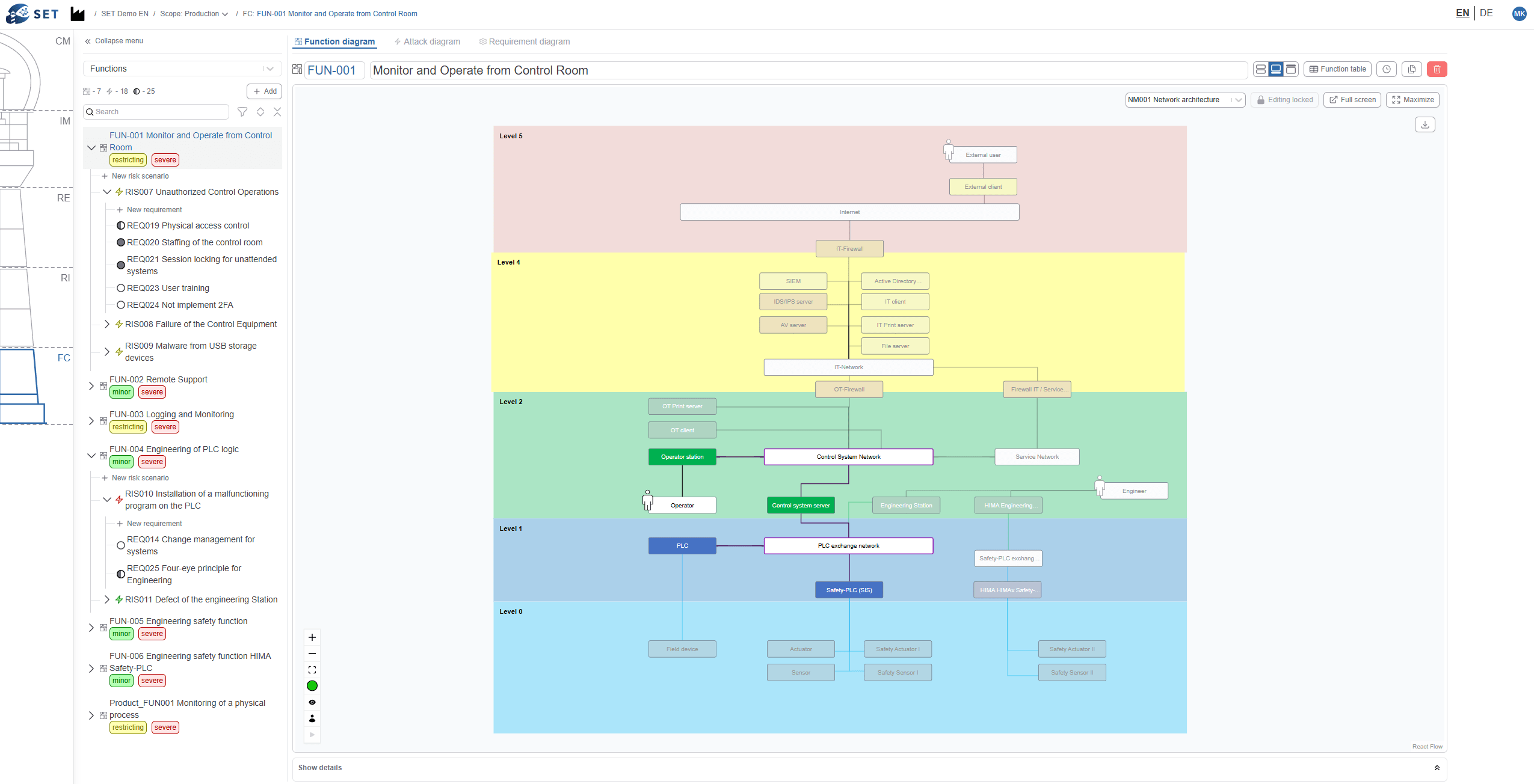
Relevant information about business, IT, and OT is spread across many departments. Without an explicitly modeled cyber system, there is no firm foundation for a structured risk assessment.
2. Risk assessments are inefficient and resource-hungry.
System experts are called on repeatedly; knowledge is exchanged manually; results are hard to replicate.
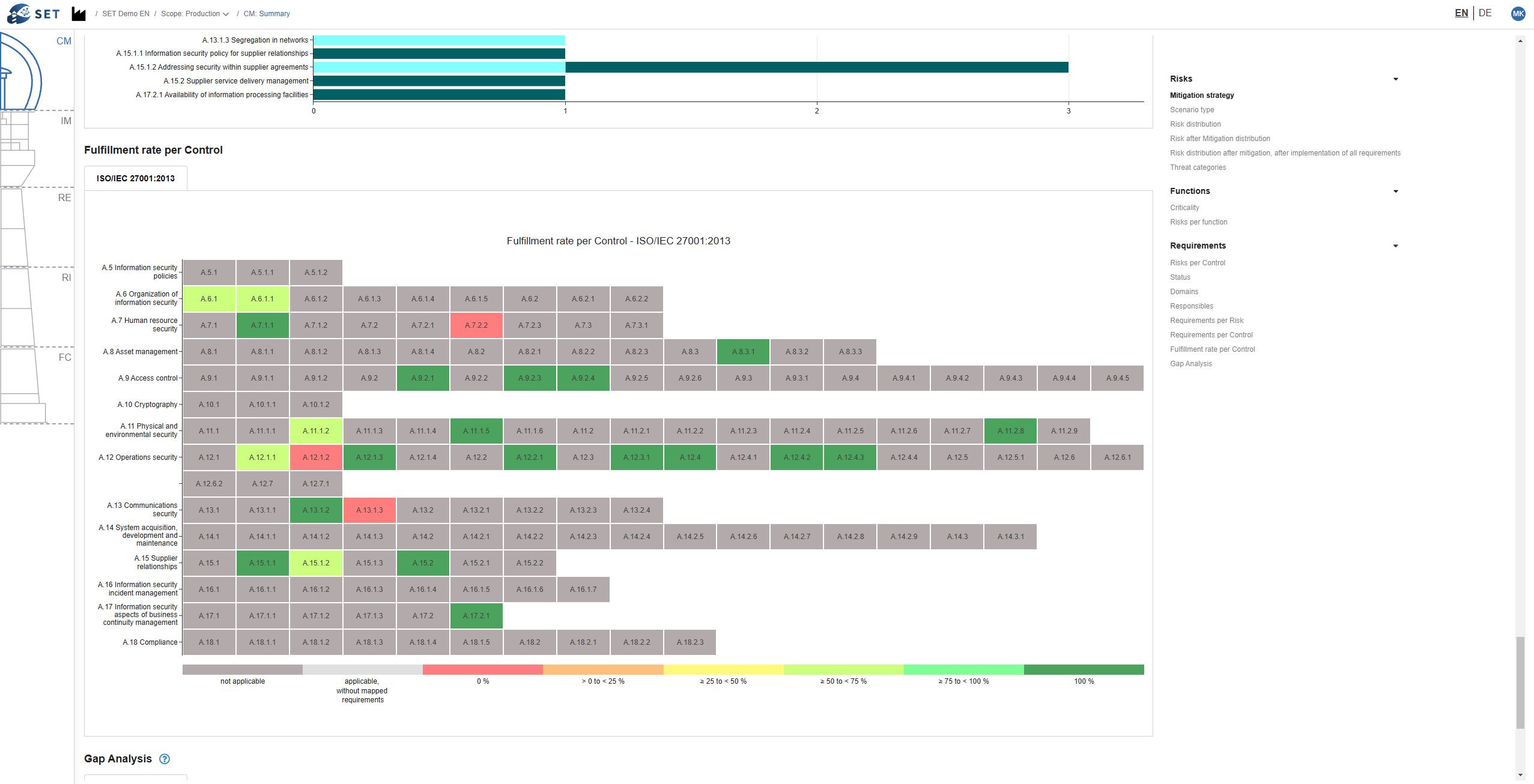
There is no structured process to consistently prioritize risks and draw logical conclusions for decision-making.
3. Decisions cannot be clearly justified.
There is no coherent and transparent line of argument between risks, measures, and regulatory requirements.
Security decisions cannot be justified convincingly to customers, suppliers, management, authorities, auditors, certification bodies, or conformity assessment bodies.
What happens when there’s no decision-making logic in cyber risk assessments?
The process eats into your time and budget, yet fails to yield a convincing, verifiable framework for decision-making.
This leads to audit discrepancies, rejected reports, and regulatory objections under NIS 2, KRITIS, CRA, or other EU requirements.
CE markings are delayed or expire—fines and personal liability risks become very real.